Introduction to Role and Access Policy Management
In AskTable, role and permission management is a critical component for ensuring data access control and security. By defining and managing roles along with their corresponding access policies, you can precisely control user access permissions to data, thereby protecting sensitive information and ensuring data compliance.
Concepts of Roles and Access Policies
Role
A role is a collection of permissions representing the responsibilities and functions of a user or a group of users within the system. By assigning different roles to users, you can control their access and operational permissions to system resources.
Access Policy
An access policy refers to the rights a user has to access certain resources within the system. By defining access policies, you can control the level of access users have to specific resources.
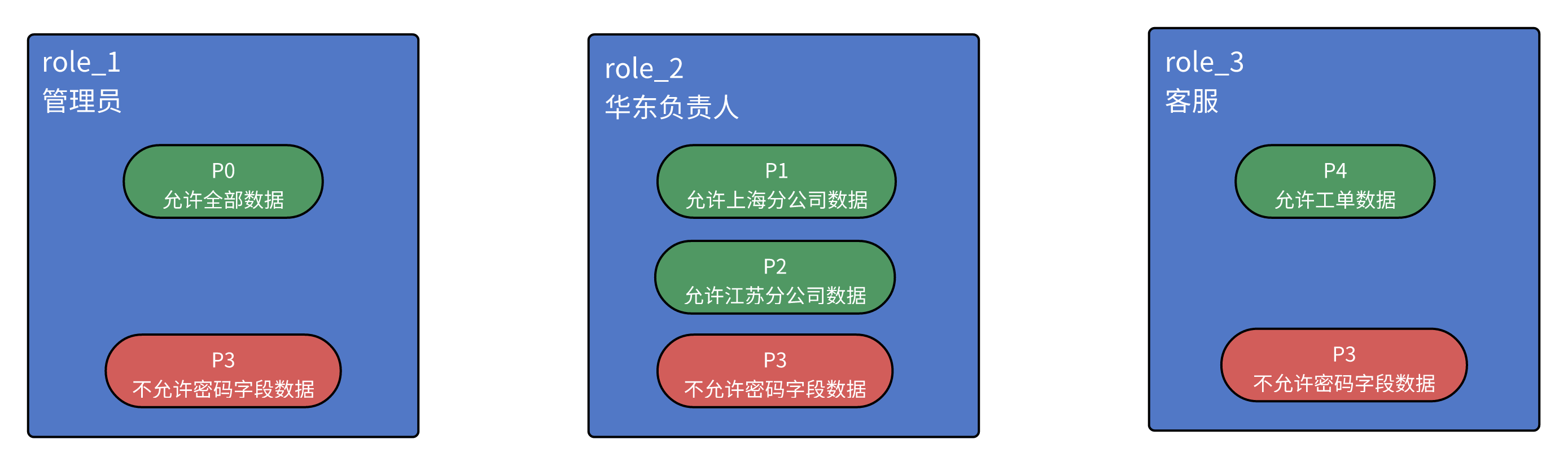
Example
In the image below, "Administrator," "East China Manager," and "Customer Service" are roles, while P0, P1, P2, P3, and P4 are policies. Each role has different access policies; for example, an "Administrator" can access all data, whereas an "East China Manager" can only access data from the East China region, and neither can access the password field.
Application Scenarios for Roles and Access Policies
- Data Protection: Ensure that only authorized users can access sensitive data, preventing unauthorized access.
- Duty Separation: Assign different roles based on user responsibilities to ensure that each user can only access data relevant to their work.
- Compliance Requirements: Meet legal regulations and industry standards to ensure compliance in data access.
Advantages of Role and Access Policy Management
- Flexibility: You can flexibly define and adjust roles and their permissions according to business needs.
- Security: Protect data security and integrity through fine-grained permission controls.
- Manageability: Simplifies the complexity of permission management, enhancing the system's manageability.
In the following documentation, we will delve into how to define access policies, create and manage roles, and use roles to access data in AskTable.